[ad_1]

We just lately reported on how a number of pirate streaming apps for iOS managed to get permitted on the App Retailer by tricking the evaluate course of. Though we briefly talked about a few of the methods utilized by these builders, 9to5Mac has now taken a deep dive into how these apps are engineered to trick Apple.
Methods utilized by builders to bypass the App Retailer evaluate
Final month, an app known as “Gather Playing cards” reached the highest of the App Retailer’s rating of probably the most downloaded free apps in some international locations. After our report, Apple took the app down – however many different variations of the identical app have been later launched on the App Retailer. However how precisely are builders in a position to trick the App Retailer evaluate group?
In our unique report, we defined that these apps use geofence to stop anybody at Apple from seeing what the app is definitely able to. However by analyzing the code of those apps, we now have a greater concept of how this occurs.
As we guessed, these apps share the identical code base – even when they’re distributed by totally different developer accounts. They’re constructed on React Native, a cross-platform framework based mostly on JavaScript, and use Microsoft’s CodePush SDK which permits builders to replace elements of the app with out having to ship a brand new construct to the App Retailer.
Constructing React Native apps and utilizing CodePush isn’t towards App Retailer guidelines. In reality, there are lots of well-liked apps that achieve this. Nevertheless, malicious builders benefit from these applied sciences to bypass the App Retailer evaluate.
One of many apps analyzed by 9to5Mac factors to a GitHub repository that appears to supply information for a number of pirate streaming apps. This app additionally makes use of a particular API to test the situation of the machine based mostly on the IP handle. It returns information such because the nation, area, metropolis, and even estimated longitude and latitude.
When the app is opened for the primary time, it waits just a few seconds to name the geolocation API. This fashion, the App Retailer’s automated evaluate course of doesn’t see something uncommon within the app’s code. We additionally checked the app’s habits by working it by means of a proxy to pretend our location to San Jose, California. For this location, the app by no means reveals its hidden interface.
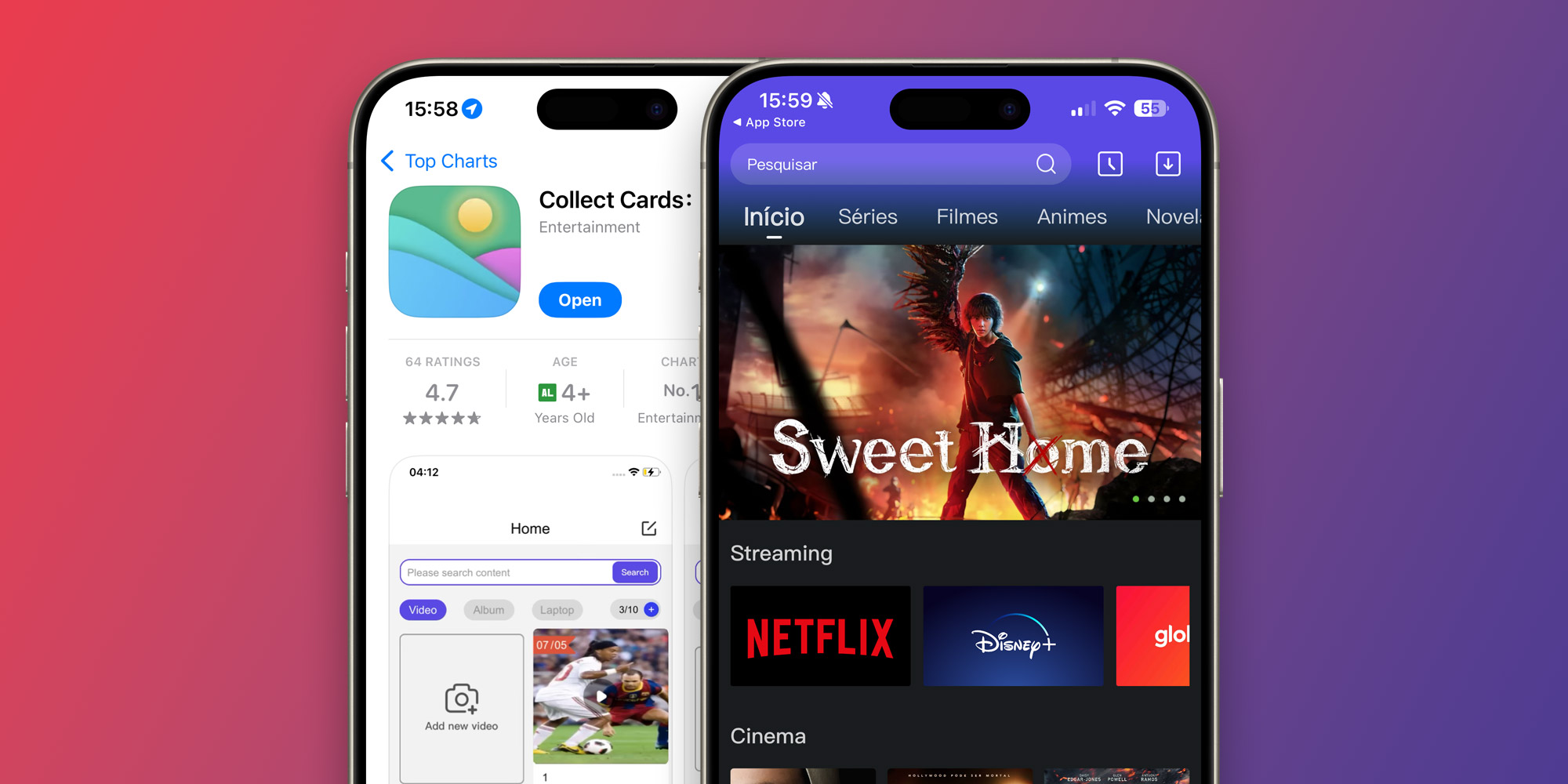
After Apple approves the app with its fundamental functionalities, builders use CodePush to replace it with something they need. The app then reveals its true interface in “secure” places.
What can Apple do about it?
After all, Apple isn’t proof against apps attempting to trick its evaluate system. Nevertheless, the corporate may enhance it by implementing extra assessments to test the app’s habits in different places. On the similar time, Apple ought to extra proactively discover and take away rip-off apps from the App Retailer.
In 2017, Uber was accused of engaged on a “geofence” for Apple’s headquarters in Cupertino. When the app was run inside this geofence, it robotically disabled codes used to fingerprint and monitor the consumer throughout the online. Even so, it appears that evidently Apple hasn’t completed a lot to stop different conditions like this.
In 2021, paperwork revealed that the App Retailer Overview group has greater than 500 human specialists to evaluate greater than 100,000 apps each week. Even so, the overwhelming majority of apps undergo automated evaluate processes to test in the event that they violate the App Retailer tips earlier than present process the handbook evaluate course of.
Following the publication of our articles, an Apple spokesperson instructed 9to5Mac that the apps have been faraway from the App Retailer, however no particulars have been offered concerning the firm’s measures to stop different apps like this from getting permitted.
FTC: We use revenue incomes auto affiliate hyperlinks. Extra.
[ad_2]
