[ad_1]
Cannot catch a break: Bear in mind BlackLotus? The same new vulnerability has now appeared, and it may very well be the following large headache for Intel-based gadgets, together with these primarily based on the newest Raptor Lake platform. It impacts the UEFI firmware, doubtlessly giving attackers a backdoor to wreak havoc on susceptible PCs.
The flaw (CVE-2024-0762 with a reported CVSS of seven.5) was found within the Phoenix SecureCore UEFI firmware by cybersecurity agency Eclypsium, who recognized it on Lenovo ThinkPad X1 Carbon seventh Gen and X1 Yoga 4th Gen gadgets. Additional investigation revealed that the vulnerability impacts SecureCore firmware for a variety of Intel CPUs, together with Alder Lake, Espresso Lake, Comet Lake, Ice Lake, Jasper Lake, Kaby Lake, Meteor Lake, Raptor Lake, Rocket Lake, and Tiger Lake.
That is each “Lake” launched to date, so a whole lot of fashions from main producers similar to Lenovo, Dell, Acer, and HP may very well be impacted.
The vulnerability is actually a buffer overflow bug discovered within the firmware’s Trusted Platform Module (TPM) configuration, which lets attackers escalate privileges and acquire code execution throughout the UEFI firmware throughout runtime. By overwriting adjoining reminiscence with fastidiously crafted information, attackers can elevate privileges and acquire code execution talents throughout the firmware, enabling them to put in bootkit malware.
“To be clear, this vulnerability lies within the UEFI code dealing with TPM configuration – in different phrases, it does not matter when you’ve got a safety chip like a TPM if the underlying code is flawed,” clarifies Eclypsium.
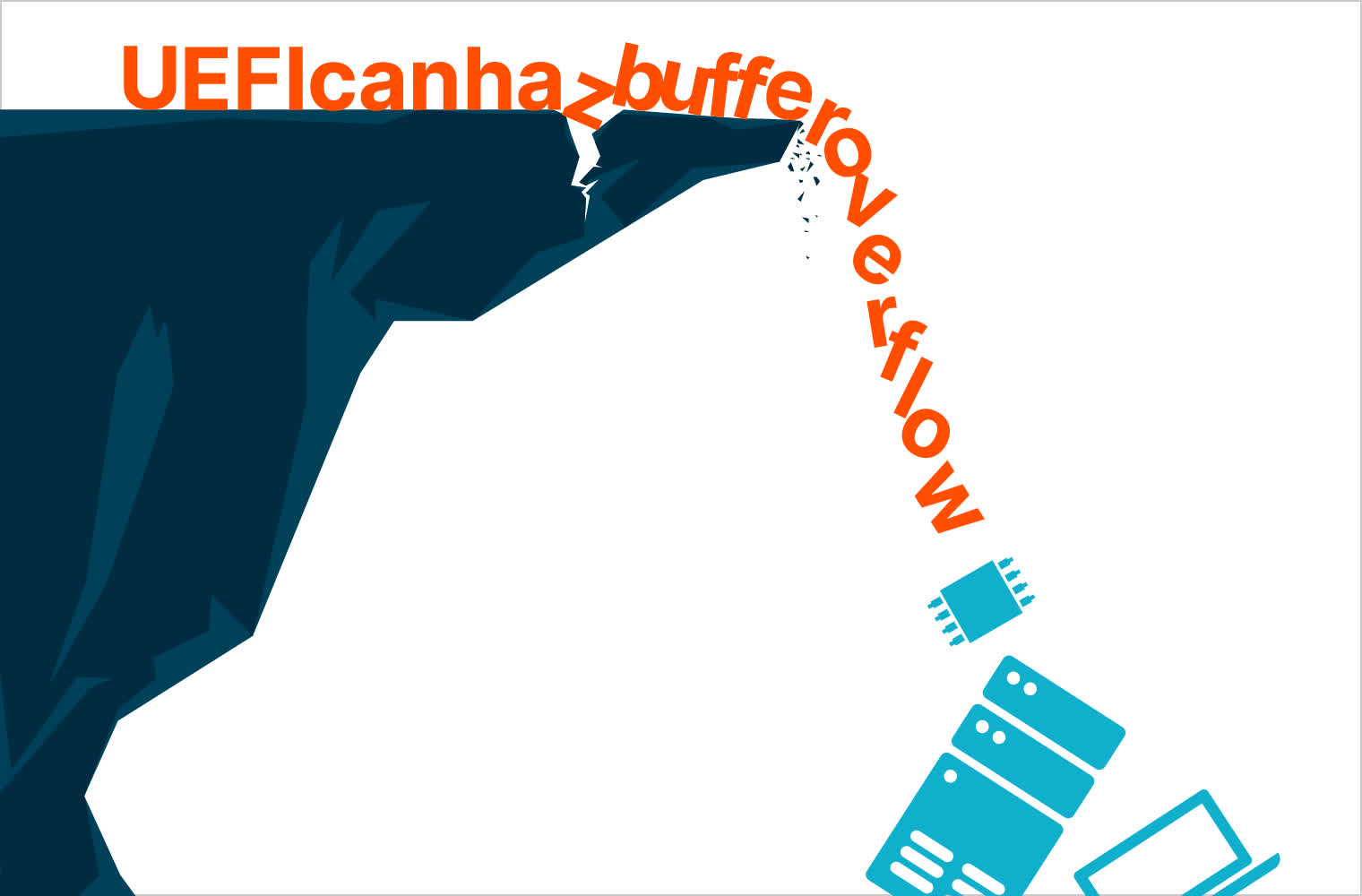
Such low-level exploits have gotten more and more widespread within the wild, offering unhealthy actors with persistent entry to gadgets and the means to work round higher-level safety measures within the OS and software program layers.
UEFI firmware is mostly thought-about safer due to Safe Boot, a characteristic supported by fashionable working techniques like Home windows, macOS, and Linux. However the discovery of this vulnerability highlights the rising pattern of focusing on UEFI bugs to create malicious bootkits. These bootkits, similar to BlackLotus, CosmicStrand, and MosaicAggressor, load early within the UEFI boot course of, granting attackers low-level entry to the system. This makes detection extremely tough.
In response to this discovery, Eclypsium coordinated with Phoenix and Lenovo to deal with the flaw. Lenovo has already launched firmware updates for affected gadgets, and prospects are suggested to seek advice from their respective distributors for the newest firmware updates. Nonetheless, you will need to word that not all fashions have accessible firmware updates on the time of writing, with many deliberate for launch later this 12 months.
When you’re an Intel person, it is essential to replace your BIOS as quickly as potential. However earlier than diving in headfirst, be certain to again up your vital information and the unique BIOS, simply in case issues go sideways throughout the replace course of.
In the meantime, Phoenix Applied sciences disclosed the vulnerability in Might, asserting that mitigations have been launched as early as April. “Phoenix Applied sciences strongly recommends prospects to replace their firmware to the newest model and speak to their {hardware} vendor as quickly as potential to stop any potential exploitation of this flaw,” it mentioned.
[ad_2]